The Role of Privacy Enhancing Technologies (PETs)
Data Minimization: The Art of Collecting Only What's Necessary
In today's digital ecosystem, the principle of data minimization forms the bedrock of effective privacy strategies. This approach advocates for gathering only the essential information required for specific operations, transforming how organizations handle sensitive data. What makes this revolutionary isn't just the reduction in data volume, but the fundamental shift in mindset regarding collection practices. Modern privacy technologies employ sophisticated methods like federated analytics and differential privacy frameworks to process information without direct access to raw data, significantly lowering exposure risks.
The concept of privacy by design has emerged as a game-changer in this space. Rather than retroactively applying privacy measures, systems are now engineered from the ground up with strict data collection limits. This proactive methodology prevents the accidental accumulation of unnecessary personal information, creating a more secure environment for users. When implemented correctly, this approach virtually eliminates the possibility of data hoarding beyond operational requirements.
Decentralization: Redefining Data Control Paradigms
The shift toward decentralized architectures represents a fundamental reimagining of data governance. Instead of relying on vulnerable central repositories, information and processing capabilities are distributed across multiple nodes. This structural innovation dramatically reduces systemic vulnerabilities while giving individuals unprecedented control over their digital footprints. The days of single points of failure are being replaced by resilient networks where no single entity holds disproportionate power.
Advanced cryptographic protocols form the backbone of these decentralized systems, ensuring security even when data moves between parties. Beyond just protection, this distributed model enhances availability and resistance to censorship - critical factors in scenarios requiring uninterrupted access without centralized gatekeepers. The true power of decentralization lies in its ability to democratize data control, creating a more balanced digital ecosystem where individuals regain sovereignty over their information.
The Powerful Synergy Between Minimalism and Distribution
When combined, these two principles create a privacy framework greater than the sum of its parts. Distributed systems naturally complement minimal data collection by reducing the information stored at any single location. This dual approach creates multiple layers of protection, where even potential breaches yield limited useful information to attackers.
The resilience of such systems comes from their segmented nature - compromising one component doesn't jeopardize the entire dataset. This architectural advantage makes decentralized, minimal-data solutions particularly attractive for high-risk environments. More than just technical solutions, these approaches represent a philosophical shift toward user empowerment in the digital age, where privacy becomes an inherent feature rather than an afterthought.
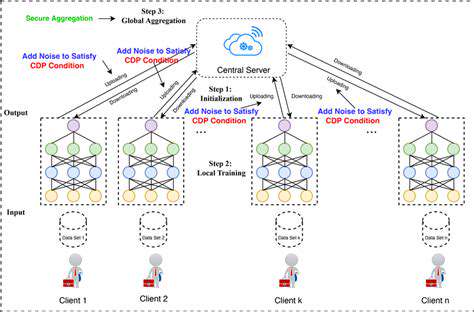
Innovative Approaches to Secure Data Processing
Federated Learning: Revolutionizing Model Training
The emergence of federated learning has transformed how machine learning models are developed. This groundbreaking technique enables collaborative training across devices while keeping sensitive information localized. By eliminating the need for data centralization, federated approaches have redefined what's possible in privacy-sensitive sectors like medical research and financial services. The ability to leverage diverse datasets without physical consolidation opens new frontiers in ethical AI development.
At its core, the federated model operates through an elegant iterative process. Local devices train using their resident data, then contribute only model updates to a central aggregator. This continuous refinement cycle preserves raw data privacy while still achieving robust model performance, demonstrating that effective machine learning doesn't require compromising user confidentiality.
Differential Privacy: The Mathematical Guarantee
Differential privacy represents one of the most significant advancements in data protection mathematics. These algorithms introduce precisely calibrated statistical noise to mask individual contributions to datasets. In sensitive domains like healthcare analytics, this mathematical rigor provides provable privacy guarantees that traditional methods can't match. While the privacy-accuracy tradeoff remains an active research area, recent breakthroughs continue to narrow this gap.
Overcoming Implementation Challenges
Real-world deployment of these technologies presents unique obstacles. Data heterogeneity across devices can impact model convergence, requiring sophisticated aggregation techniques. Communication overhead presents another critical challenge, driving innovation in compression and update optimization protocols. These practical considerations are shaping the next generation of privacy-preserving systems.
Transformative Applications Across Industries
The potential applications span numerous sectors. Healthcare systems can develop predictive models without compromising patient records. Financial institutions can detect fraud patterns while maintaining client confidentiality. These real-world implementations demonstrate how privacy technologies can enable innovation rather than restrict it, creating new possibilities across the digital landscape.

Navigating the Privacy Landscape of Tomorrow
The Growing Imperative for Data Protection
As digital interactions multiply, personal data has become the lifeblood of modern economies. This exponential growth in data collection demands equally sophisticated protection mechanisms, creating an urgent need for advanced privacy solutions. The ethical implications of data usage are coming into sharp focus, with individuals increasingly aware of their digital rights.
Technological Solutions for Emerging Challenges
Innovation in privacy technologies is keeping pace with these challenges. Breakthroughs in homomorphic encryption now allow computations on encrypted data, while zero-knowledge proofs enable verification without information disclosure. These cutting-edge solutions are redefining what's possible in secure data processing, offering hope for maintaining privacy in an increasingly transparent world.
Pseudonymization Techniques in Practice
Modern pseudonymization goes beyond simple identifier replacement. Advanced techniques now incorporate dynamic re-identification barriers and context-aware protection layers. When properly implemented, these methods create robust safeguards against unauthorized data linkage, particularly valuable in longitudinal studies and cross-institutional research.
The Regulatory Landscape Evolution
Global privacy regulations continue to evolve, with newer frameworks emphasizing both individual rights and organizational accountability. The maturation of these laws reflects growing international consensus on fundamental data protection principles. This regulatory evolution is driving technological innovation as organizations seek compliant solutions that don't sacrifice functionality.
AI Ethics and Privacy Preservation
The intersection of artificial intelligence and privacy presents both challenges and opportunities. Responsible AI development now requires privacy considerations at every stage, from initial design to deployment. Techniques like federated learning and differential privacy are proving particularly valuable in creating AI systems that respect user confidentiality while delivering powerful insights.
Read more about The Role of Privacy Enhancing Technologies (PETs)
Hot Recommendations
- Personalizing Email Content with User Behavior
- Geofencing for Event Attendance Tracking
- Reputation Management on Social Media
- UGC Beyond Photos: Videos, Testimonials, and More
- The Future of Data Privacy Regulations
- Accelerated Mobile Pages (AMP) Benefits and Implementation
- The Future of CRM: AI and Voice Integration
- Google Ads Smart Bidding Strategies: Maximize Value
- Common A/B Testing Pitfalls to Avoid
- Local SEO Strategies for Small Businesses